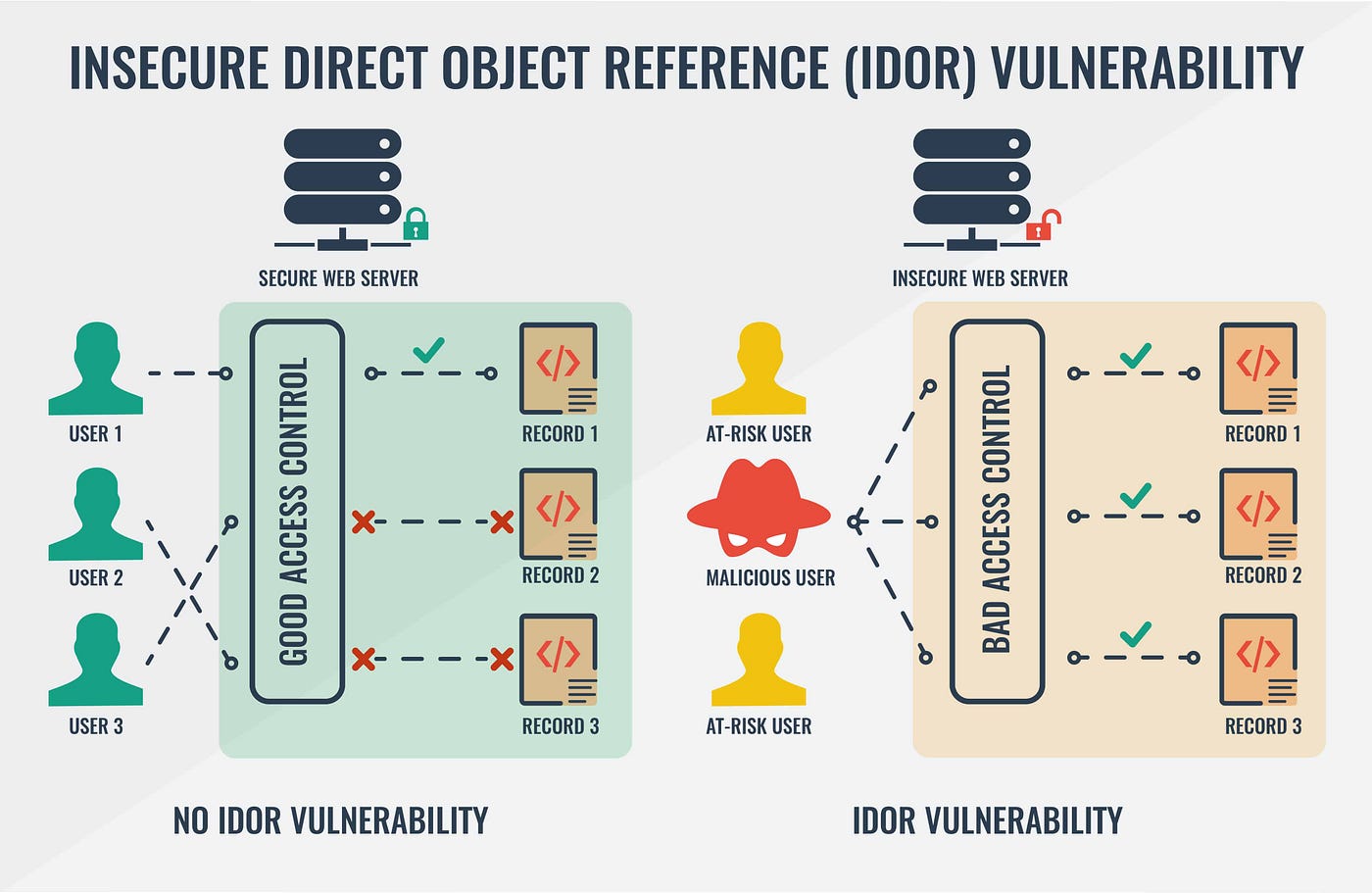
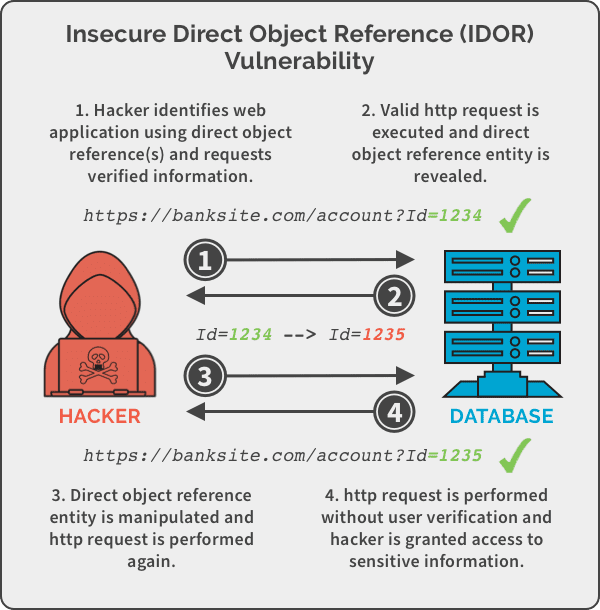
IDOR (Insecure Direct Object References) is a type of security vulnerability that occurs when an application exposes references to internal objects (such as files, database records, or user data) without properly validating whether the user is authorized to access them. In simpler terms, IDOR vulnerabilities arise when a user is able to access or manipulate resources (objects) that they shouldn’t be able to by modifying an identifier in a request (e.g., a URL, form field, or API parameter).
IDOR implementation involves protecting against this vulnerability by enforcing strict access control measures and ensuring that users can only access the data they are authorized to interact with. This is done through various techniques and strategies like authorization checks, dynamic resource validation, and proper error handling.
Protection of Sensitive Data: IDOR vulnerabilities can allow unauthorized users to access sensitive information (like private account details, health records, or financial data). For example, in a healthcare application, IDOR vulnerabilities could let attackers access private medical records of patients.Protecting against IDOR ensures that users can only access data meant for them, safeguarding privacy and compliance with regulations like GDPR and HIPAA.
Preventing Unauthorized Actions: If an attacker can modify an identifier to access another user's data, they may also be able to modify that data. For example, they could delete, update, or create new records. In an e-commerce application, this could allow an attacker to change order details or payment information, resulting in fraud or malicious actions. IDOR protection ensures that users can only perform actions on objects that they are authorized to interact with.
Securing APIs: Many modern applications rely on APIs to communicate between the frontend and backend. APIs often accept object identifiers in the form of parameters. Without proper validation, attackers can manipulate these parameters to access unauthorized resources, leading to data breaches. Protecting APIs from IDOR is critical to ensure that only authorized users can interact with them.
Maintaining User Trust: Users trust applications with their sensitive data, and any breach or unauthorized access undermines this trust. By implementing IDOR protection, developers demonstrate their commitment to security, which is crucial for retaining users and maintaining a positive reputation.